Sucuri, a company specializing in IT security, has published its quarterly report Website Hacked Trend examining the second quarter of 2016. WordPress remains the most targeted content manager, largely due to a lack of training of website administrators or their negligence.
The first ranking supplied by Sucuri pertains to the proportions of the different types of CMS platform appearing in the sample set of infected websites. Not surprisingly, WordPress remains at the top of the list, accounting for three fourths (74%) of all infected sites, despite a slight improvement (by 4%) over the previous quarter. Joomla now represents 16.2% of infected sites, up 2.2%. The other platforms’ shares were stable since the report was last published.
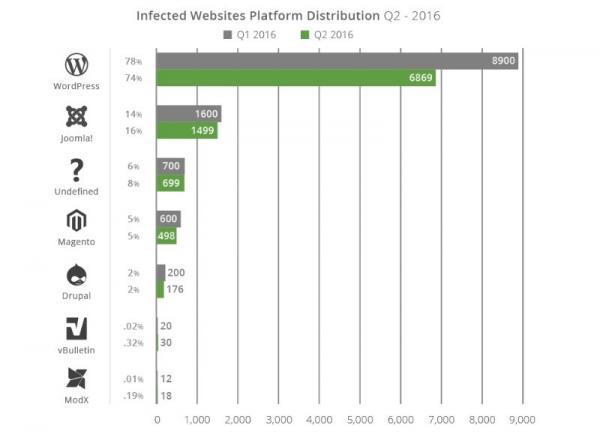
This diagram does not claim to describe the platforms’ level of security. Generally speaking, the problems observed on websites do not come from the platform, but are rather linked to site rollout, configuration and maintenance issues. With a market share of close to 50%, WordPress is the obvious choice of target for malicious people whose efforts will pay off more quickly given its widespread use.
Although extensions and other plug-ins are the primary sources of security breaches, Sucuri’s report highlights a direct correlation between the lack of website updates and site vulnerability.
On this subject, WordPress is actually doing fairly well compared to the competition. The other CMS platforms are having real problems getting site administrators to apply their updates. In the case of Magento, nearly 96% of attacks are linked to a lack of maintenance. Sucuri has identified three likely causes of this phenomenon: highly personalized rollouts that make the application of updates tedious work, problems with backward compatibility that prevent some websites from enjoying the benefits of security patches and, in more pragmatic terms, a lack of personnel dedicated to site migration.
The Sucuri report pays special attention to WordPress, with 74% of the sample websites running on the platform. Nearly one fourth (22%) of the vulnerabilities observed on the platform stem from the use of three out-dated plug-ins: TimThumb, RevSlider and Gravity Forms.
For the first time, Sucuri expanded its quarterly report to include data on blacklisted infected sites and the actors involved in that process. Sucuri remarks: “Understanding how blacklists work, and how they affect a website’s brand reputation is important and should be a data point every website owner should monitor”. Obviously, a site flagged by Google will lose its search results ranking and its methods of communication will be affected, including access to the site itself which becomes more difficult.
In the sample set analysed by Sucuri, 18% of the infected sites had been blacklisted. This is a very low proportion in view of the remaining 82% of websites which can continue to distribute malware with no warning given to users. There is a lot of room for progress to be made in respect of the different search engines and hosting platforms. Half the blacklisted sites (52%) were detected by Google Safe Browsing, while Norton and Yandex detected 30% of them and SiteAdvisor 11%.
Affected sites can be hit by various families of malicious processes, depending on the attacker’s intentions. In this latest report, Sucuri found that 71% of attacks on the sample group came through PHP-based backdoors hidden within the site. This method, which consists of preserving access to the website well after it was hacked, allows the attacker to bypass any access controls. It is also especially difficult to detect using website scanning technologies. These backdoors may not even present any external signs of modification of the site, making the attack invisible to visitors.
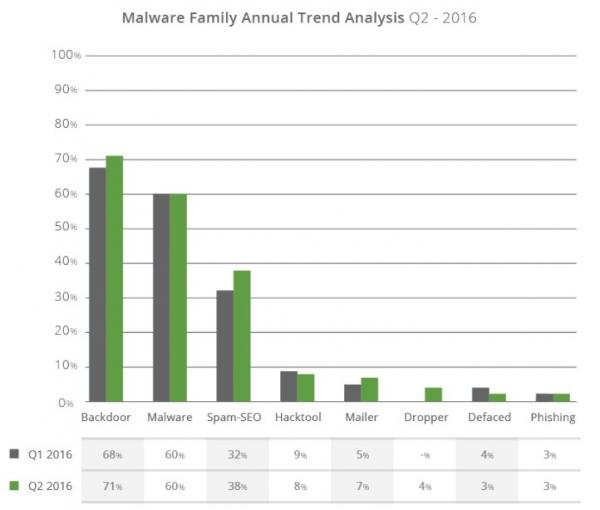
This type of hack, which has increased since the previous quarter, is often a precursor to a second nefarious act that aims to harvest the fruit of the intrusion through the propagation of malware, malicious redirects, phishing, and so on.
Source: sucuri.net